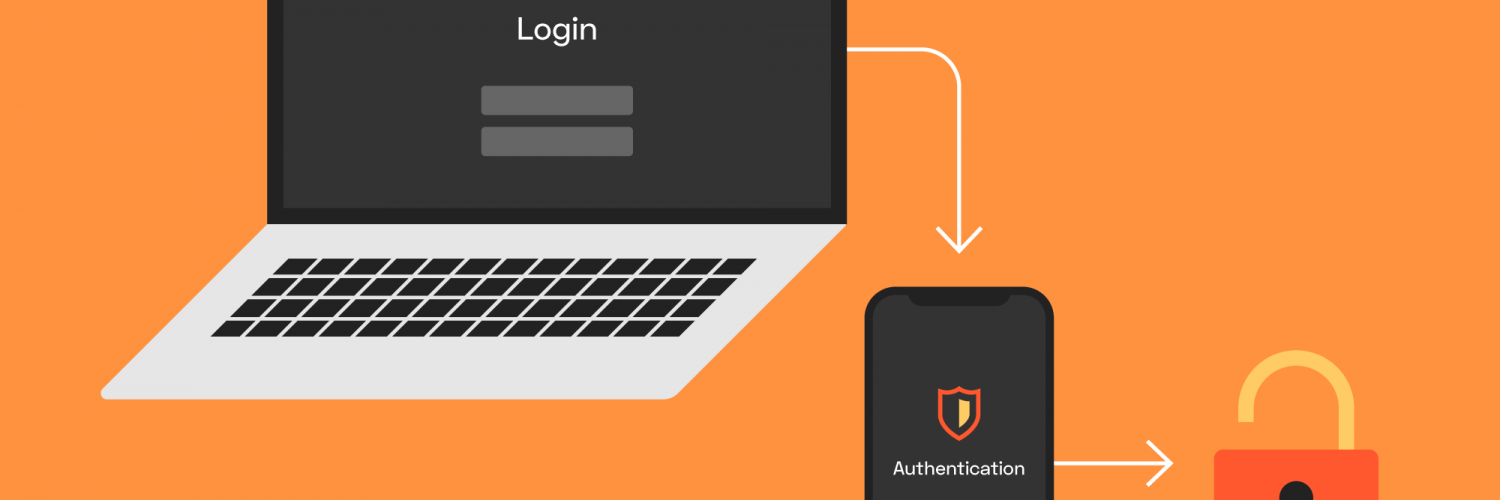
Two-factor (2FA) and two-step (2SV) authentication are ways to further protect your account. Often, even developers put an equal sign between them. But this is not true.
What is two-factor authentication?
The key word here is factor. There are four of them:
knowledge of something – for example, username, password, key, passphrase, any other secret information that is set when creating a profile;
possession of something – for example, a hardware token or a smartphone with an application that generates codes;
being in a specific place – for definition, it is used, for example, the user’s IP address or a radio tag;
possession of certain biological characteristics – for example, scanning a fingerprint or an iris of the eye.
Two-factor authentication is when two factors are used sequentially.
For example, I have a Yandex account with two-factor authentication enabled in its settings. To enter it on a new device, two factors must be met:
I know the login.
I have a smartphone with the Yandex.Key app, which generates codes for authorization.
There are other apps for generating codes: Google Authenticator, Microsoft Authenticator, LastPass Authenticator. But they all solve one problem – they act as the second factor in user authorization.
Instead of a smartphone with an app, you can use a hardware token. It connects via USB, Bluetooth or NFC. When you register for the next service and enable two-factor authentication, a new key pair is generated inside the token. The public key is transmitted to the server, the private key is stored on the hardware token.
How is two-factor authentication different from two-factor authentication?
Dynamically utilize resource sucking partnerships rather than fully tested outsourcing. Dynamically negotiate principle-centered sources with client-based e-tailers. Globally deploy high-quality initiatives with cross-unit initiatives. Holisticly provide access to cross functional web services with user-centric customer service.